Configuration
Using the Verisys console, agents can be configured to monitor specific files or groups of files using wildcards, and can recurse through a directory structure. You may have different monitoring requirements for some objects (for example you may wish log files to be able to grow but want to detect any alterations to previously logged data). Verisys accordingly allows to you configure different monitoring levels to give you control over what properties are observed.
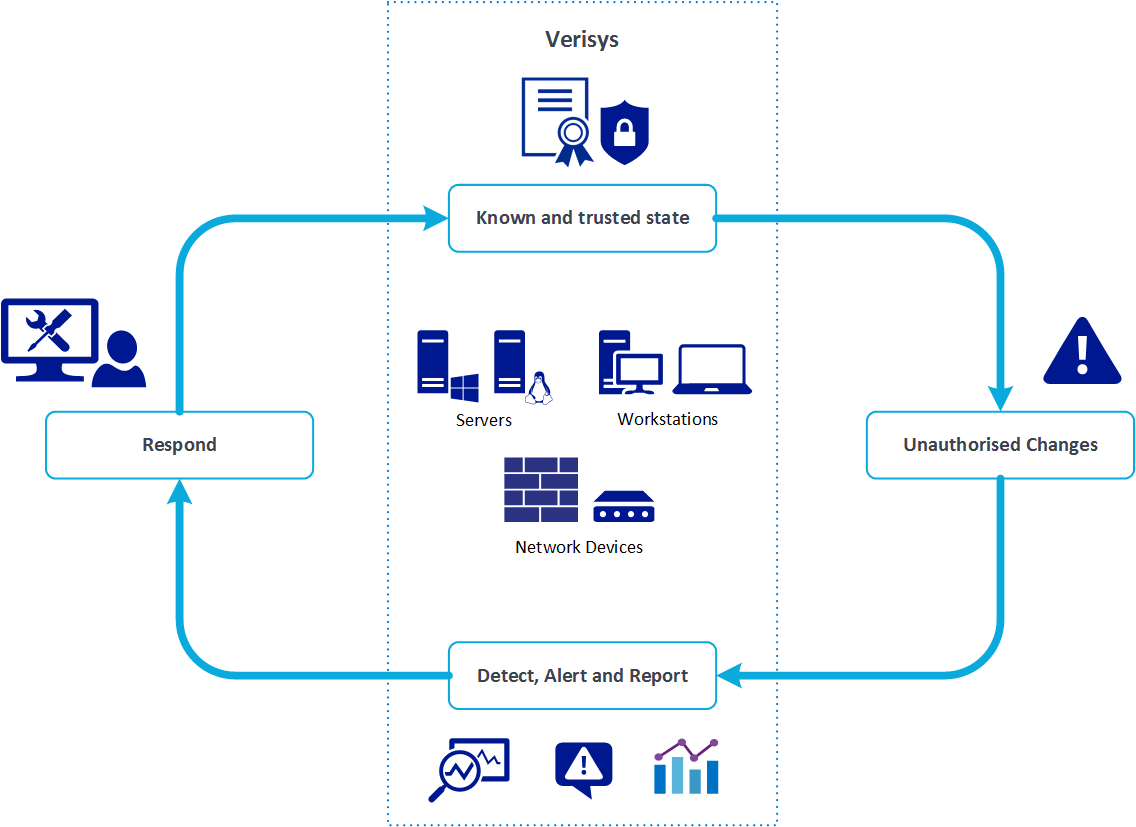
In your environment some system objects may be more critical than others, so Verisys allows you to set a priority for each monitoring rule, enabling different actions to be taken automatically. To find out more about Verisys reporting and alerting capabilities, click here.
Operating system and application templates for common system configurations are included to help you get started: